Privacy and Cybersecurity — Extending the Cybersecurity Defense
Publication | 01.19.16
Faced with growing cybersecurity threats, federal agencies are rethinking regulations to strengthen networks in both the government and private sectors.
A key effort on this front is the Department of Defense’s (DOD) Defense Federal Acquisition Regulation Supplement (DFARS) Safeguarding Rule, which applies to defense contractors. The rule requires contractors to implement dozens of specific security controls in information systems that contain unclassified controlled technical information (UCTI), generally defined as scientific or technical data related to space or military uses. It also requires contractors to notify the DOD if those systems are compromised to the extent that the UCTI could be affected.
The Safeguarding Rule’s mandates are to be included in all department solicitations and contracts, including those covering commercial items. But that has not been the case. The rule has been in effect since late 2013, but implementation in DOD contracts has been inconsistent.

However, in February 2015, “the DOD criticized its component organizations for not adequately incorporating the rule into their contracts. That was a clear reminder that this is mandatory,” says Evan Wolff, co-chair of Crowell & Moring’s Privacy & Cybersecurity Group and a former advisor at the Department of Homeland Security (DHS).
Those mandatory requirements became more complex in August 2015, when the DOD released a revised version of the Safeguarding Rule. The new version requires contractors to implement an expanded set of security controls. And those controls are now mandatory on information systems containing not just UCTI but also other forms of “covered defense information,” such as information critical to operational security.
This—combined with the DOD’s February statements—suggests that the defense industry will be keeping a close eye on contractor compliance. Companies are likely to see an increased number of federal contract modifications to include the rule after the fact, as well as tighter enforcement of the rule by the DOD.
Contractors working with non-defense agencies will soon be facing similar requirements. Many federal agencies are considering cyber regulations related to procurement. For its part, the Office of Management and Budget (OMB) recently proposed cybersecurity guidelines—similar to the DOD rule—that would apply to all federal contractors. The OMB would like these guidelines to be incorporated into the Federal Acquisition Regulation and adopted by the General Services Administration and other agencies.
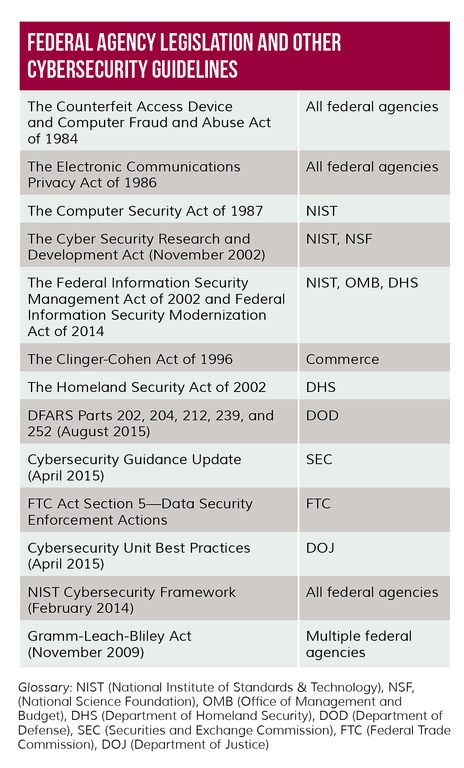
The impact of evolving cybersecurity regulations is also beginning to reach corporations well beyond the government contracting sphere. “We’re seeing a wide variety of agencies across the federal government, including DOJ, FTC, FCC, SEC, and DHS, using their current regulatory authority or seeking additional authority to regulate cybersecurity activities in the private sector at large,” says Wolff.
The growing focus on cybersecurity creates challenges for companies, but some regulations are making it easier to secure private sector systems. The DHS Support Anti-Terrorism by Fostering Effective Technologies (SAFETY) Act program, for example, limits tort liability arising out of acts of terrorism when companies have implemented DHS-approved security technology. Enacted as part of the Homeland Security Act of 2002, the SAFETY Act has been applied to physical security-related technologies, such as scanners and metal detectors. But in 2015, DHS began including cybersecurity technologies in the program, with the approval in April 2015 of cyber-threat detection technologies from the Fire Eye company. “That approval is likely to encourage other technology companies to seek approval for their cybersecurity tools as well,” says Harvey Rishikof, senior counsel in Crowell & Moring’s Privacy & Cybersecurity Group. “And because the liability protections flow up and down the chain, it may motivate companies to purchase and use the approved technologies.”
Overall, the federal government’s broadening view of cybersecurity is based on the fundamental recognition that “national security information isn’t just held in places like the CIA or the military,” says Wolff. “Today, it’s also at agencies like the Patent Office or the FDA. And it’s in the private sector—companies are on the front line here. So federal agencies are realizing that not only are their systems at risk, they also need to focus on their supply chain.”
“With this growing scrutiny on the private sector, the general counsel now needs to be a critical advisor to the CEO about how to approach the cybersecurity issue and in taking up the issue with the board to allow for proper oversight,” says Rishikof. “The general counsel needs to make sure the company is seeing this not just as an IT risk but as an enterprise risk that needs to be managed through an appropriate governance structure.”

Working Toward EU-wide Standards
The European Union (EU) is negotiating a Network and Information Security Directive, commonly known as the “Cybersecurity Directive.” The negotiators of the European Parliament, Council, and Commission reached a political agreement on the text on Dec. 8, 2015, and the Directive is expected to be officially adopted by early 2016, at which point it should be implemented in the laws of EU member states over the following 21 months, after which the Members States will have another six months to identify operators of critical infrastructure. “This will be the first time that there are general Europe-wide information security standards in place,” says Frederik Van Remoortel, senior counsel at Crowell & Moring.
The Directive will primarily affect governments, spelling out security provisions that they need to implement. “It will have an impact on private sector companies as well,” notes Van Remoortel, “placing mandatory security breach and incident-notification requirements on critical infrastructure operators. The Directive will also impose security measures and notification requirements on important digital businesses, which include online marketplaces, cloud computing services, and search engines. Their obligations are said to be less stringent than those imposed on the essential services operators. The exact details will also depend on how EU member states implement the Directive in their laws.” The new Directive, he adds, “should be viewed alongside the new General Data Protection Regulation that is expected to be ratified by early 2016, which also holds general data-breach notification duties.”
[PDF Download: 2016
| |
[Web Index: 2016 Regulatory
|
[Glossary: NIST (National Institute of Standards & Technology), NSF, (National Science Foundation), OMB (Office of Management and Budget), DHS (Department of Homeland Security), DOD (Department of Defense), SEC (Securities and Exchange Commission), FTC (Federal Trade Commission), DOJ (Department of Justice)]
Contacts
Insights
Publication | 11.24.25
Litigation Funders Looking to Invest in Law Firms Face Hurdles
Publication | 11.19.25
Who Can Fix It? Antitrust, IP Rights, and the Right to Repair
Publication | 11.14.25
Three Steps Tech Companies Can Take Today To Prepare To Ride A Blue Wave In 2026



