Privacy and Cybersecurity - Data Breaches: Opening the Floodgates for the Plaintiffs' Bar
Publication | 01.19.16
Corporate information systems are being targeted by criminals, hacktivists, employees, and even nations. As these attackers expand their efforts, breaches—and litigation—continue to rise.
"Companies with personal data or trade secrets are under persistent and relentless attack," says Crowell & Moring partner Jeffrey Poston, co-chair of the firm's Privacy & Cybersecurity Group. No industry is immune. From retailers to auto manufacturers to financial institutions, U.S. and global companies are in the crosshairs. Government agencies have also experienced breaches.
Even university systems are a focus of cyberthieves. "Universities are often a goldmine of valuable data," says Poston. "They have personal information about students and employees, health information if they have medical facilities, and trade secrets and technical data if they do R&D."
Across industries, such breaches are leading to more litigation. "The plaintiffs' bar is very active in this area," says Poston. "And because breaches can involve the personal information of thousands or millions of people, we are likely to see even more class action lawsuits filed in the coming year." Significant breaches can also attract the attention of both federal and state regulators, as agencies show increased interest in cybersecurity and the protection of consumer information. These lawsuits are not limited to incidents targeting consumer data. With the rise of the Internet of Things, intrusions into an array of devices are giving rise to lawsuits alleging negligence and product liability claims.
The growing number of highly publicized breaches is also giving plaintiffs another tool in litigation. "If other companies in your industry have been attacked and then you have a breach, there is surely going to be a plaintiff's line of inquiry asking what, if anything, you did when you heard about your competitor being hacked five months ago," says Poston. "Have you implemented any of the lessons learned from the previous attack in your own organization? Already, class actions in this space reference prior incidents, such as the breaches at Sony, even though the company being sued wasn't involved in those incidents."
In this environment, companies need to ensure that they have effective security policies that not only meet regulatory requirements but also acknowledge the current state of threats. At the same time, they need to prepare for the worst, with an incident response plan that anticipates these attacks and plans for the investigation, protection of customers and the company, and remediation efforts that need to follow a data breach or cyber incident. The incident response plan should be supplemented with tabletop exercises to develop an organization's "muscle memory." "This will be an ongoing threat," says Poston. "Compliance and incident response teams should be meeting now to prepare for what may come."
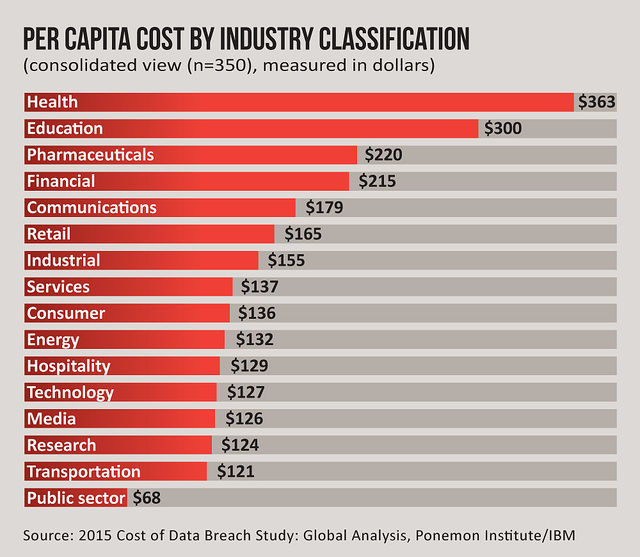
[With information systems across industries under relentless attack, data breaches can be very costly for the companies that are hit.]
[PDF Download: 2016
| |
[Web Index: 2016 Litigation
|
Contacts
Insights
Publication | 03.01.26
Publication | 02.19.26
The QICDRC Practice Direction on the Use of Artificial Intelligence
Publication | 02.06.26



