Landmark Amendments to Singapore’s Cybersecurity Bill: Re-Interpreting CII to Bolster National Cyber Resilience
Client Alert | 14 min read | 01.04.24
On 15 December 2023, the Cyber Security Agency of Singapore (CSA) opened stakeholder consultation on its draft Cybersecurity (Amendment) Bill 2023. This draft Bill is the first review of the Cybersecurity Act 2018 and aims to enhance Singapore’s cyber resilience in the face of the country’s increasing digitalization.
CSA has introduced some novel provisions in this Bill, reinterpreting how critical information infrastructure (CII) is defined, identified, and secured so as to enhance Singapore’s overall cybersecurity posture. If passed in its current form, the Bill would set important precedents for regulating such entities in the region, as other Southeast Asian nations tend to benchmark Singapore’s legislations, especially in fast-evolving fields such as cybersecurity and artificial intelligence.
Strengthening Cybersecurity for Existing CII
The Bill proposes expanding CII obligations to cover computing vendors of essential service providers. While these vendors are not necessarily providers of essential services themselves, they nevertheless manage the outsourced computing systems – both in Singapore and abroad – on which these essential services are increasingly relying. Such computing systems are thus classified as “non-provider-owned CII” in the Bill’s new provisions. Responsibility for the cybersecurity of essential services will still rest with the ultimate provider of those essential services, whose internal computer systems are already regulated under the current Act. But now these providers will also be required to obtain legally binding commitments from vendors of non-provider-owned CII to remain compliant with the Act’s expanded application. This expansion will include requirements for non-provider-owned CII around cybersecurity standards, incident reporting, auditing, and risk assessments, which parallel those already in place for providers. In other words, wherever in the supply chain lies the risk of digitally interrupting essential services, the same cybersecurity expectations will apply.
In a further attempt to enhance CSA’s insight into the cyber posture of essential services, the Bill also proposes expanding the scope of reportable incidents for providers. Under the current Act, providers are required to report incidents potentially affecting their CII, scoped in part by the logical connections between the network suffering the incident and the CII. But the current proposal adds a new trigger for providers to report incidents on any part of the network under the provider’s control, seemingly without any logical nexus to the provision of CII.
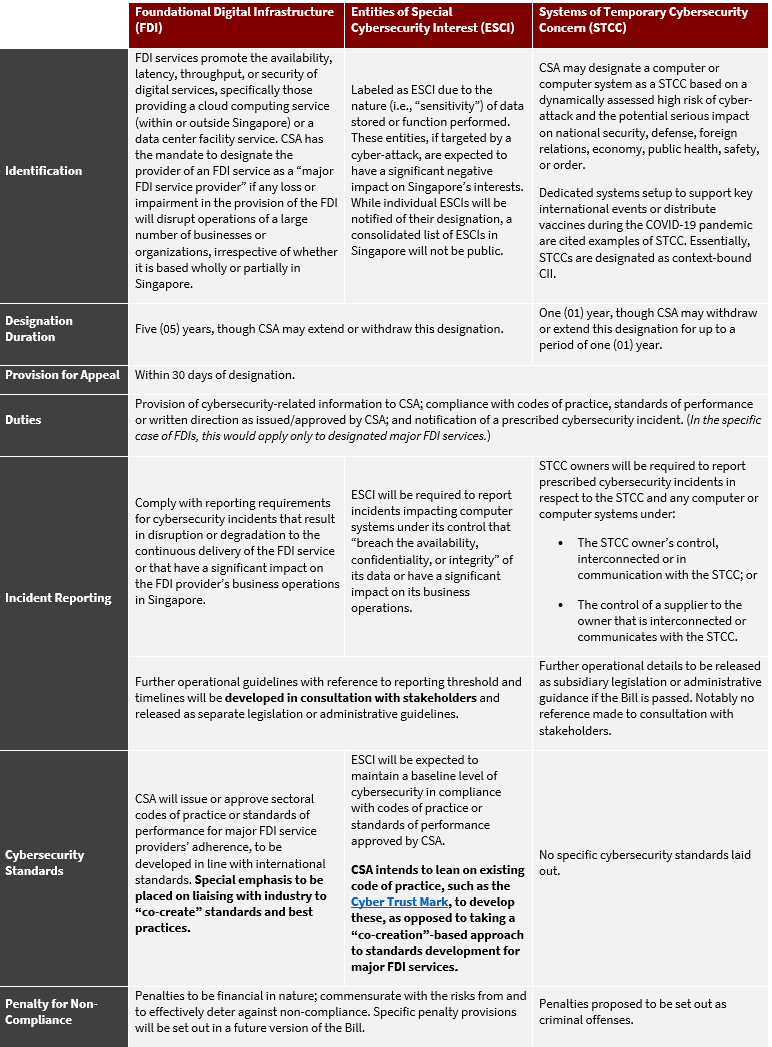
Looking Beyond CII
This Bill also widens CSA’s purview to include computer systems not strictly classified as CII in the 2018 version or as non-provider-owned CII under the new Bill, if they fall under the below three categories:
Other Amendments
Under Part 5 of the Act, individuals in the business of providing licensable cybersecurity services will be required to obtain or renew a cybersecurity service provider’s license, subject to conditions set by the Licensing Officer. In response to reports of unauthorized individuals falsely claiming to represent CSA for fraudulent activities, a new amendment will explicitly state that only CSA has the exclusive right to CSA’s symbols or representations.
Our Take
This is a forward-looking amendment seeking to address the diverse range of growing cybersecurity vulnerabilities in Singapore’s digital economy. But tackling that diversity is challenging to do in a light-touch regulatory environment. The result is a highly flexible proposal that grants significant discretion to CSA to assess and regulate the current state of the public’s cybersecurity exposure. To do that as efficiently and effectively as possible, CSA is wisely seeking industry feedback.
The business community, for example, would benefit from more clarity on definitions and compliance requirements, specifically those pertaining to the newly-defined entities. The Bill is unclear on how companies will be evaluated for designation as ESCIs or STCCs, making it harder to anticipate whether they are approaching a threshold with significant operational and compliance implications. It is also unclear how the designations may interact and/or overlap.
CSA is soliciting comments on these amendments by 5:00 pm (SGT), 15 January 2024 via its online forum. Regardless of whether the Bill becomes law, its mere proposal has established an important benchmark that will be considered globally, as the rest of the world similarly struggles with how to mitigate the risks of our growing digital footprint. Engaging now in the public-private dialogue is key to ensuring that those mitigations are informed and ultimately helpful.
We would like to thank Caitlyn Weeks, Research Associate, for her contribution to this alert.
Contacts

Partner, Crowell Global Advisors Senior Director
- Washington, D.C.
- D | +1.202.624.2698
- Washington, D.C. (CGA)
- D | +1 202.624.2500
Insights
Client Alert | 3 min read | 02.26.26
FERC Requires Refunds for Late QF Recertification
On February 19, 2026, the Federal Energy Regulatory Commission (FERC) issued Branch Street Solar Partners, LLC et al., 194 FERC ¶ 61,124 (2026) rejecting the refund reports filed in connection with the late filing of recertifications of qualifying facility (QF) status by certain affiliated companies to reflect a change in upstream ownership. FERC’s rearticulation of QF recertification timing requirements and consequences for late QF recertifications has broad and substantial implications for all QF owners.
Client Alert | 4 min read | 02.26.26
Client Alert | 6 min read | 02.24.26
Artificial Intelligence and Human Resources in the EU: a 2026 Legal Overview
Client Alert | 3 min read | 02.24.26
DOJ v. OhioHealth Confirms Antitrust Enforcers’ Continued Focus on Health Care Markets




